End-to-End security
Kontron delivers comprehensive security solutions that minimize the attack surface of your physical or virtualized network infrastructure, it ensures your critical systems, protects your sensitive data and helps you meet local and international regulatory requirements.
As a network foundation for multiple industries, SD-WAN brings comprehensive security features such as End-to-End Encryption, resilient infrastructure, integrity checks, segmentation, strong authentication method & role base access control. It's an important element of network security but has to be considered in an overall security strategy that may differ between various industries.
SECURITY FOR IT DOMAIN
Security is considered end to end. From the end device to the Cloud and to legacy data center with a set of on prem or Cloud-delivered services. Complementary to highly secured SD-WAN, those services include NGFW (Next Generation Firewall Service), ZTNA (Zero Trust Network Access), SWG (Secure Web Gateway Service), CASB (Cloud Access Security Broker), RBI (Remote Browser Isolation) and DLP (Data Leak Prevention). Such features are part of a SASE (Secured Access Service Edge) solution. SASE architecture converges network security services into a cloud-based platform, centering on the identity of users, devices and applications.
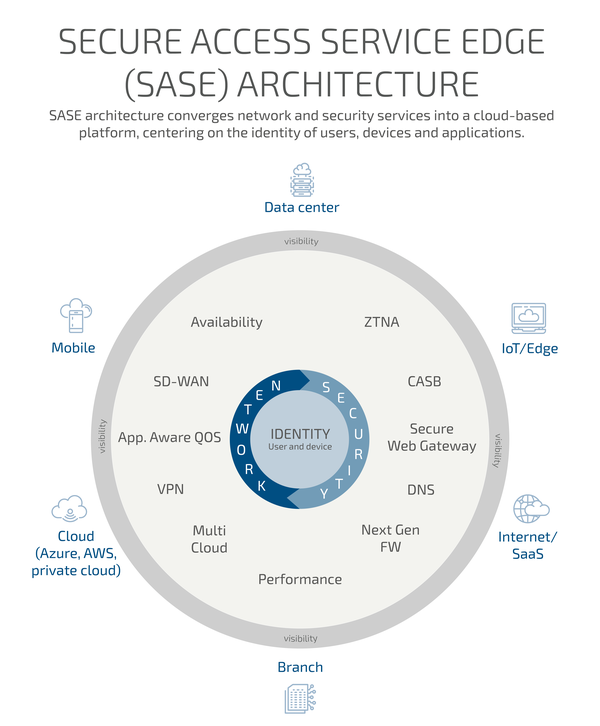
Kontron aligns its proposal with customer expectations including integration of customer existing Cyber Security service. Secured SD-WAN can be completed with cloud-based data security services such as Zscaler, Palo Alto or any other physical or virtual NGFW from major suppliers.
SECURITY FOR OT DOMAIN
According to Gartner, Operational Technology (OT) is hardware and software that detects or causes a change through the direct monitoring and/or control of physical devices, processes and events in the enterprise. Industrial Control Systems (ICS) such as a SCADA system may be used to control power stations or public transportation. As this technology advances and converges with networked tech including SD-WAN, the need for additional OT specific security is growing exponentially.
To complete traditional network or SD-WAN network infrastructure, Kontrons offer is two-folded:
- Secure Xchange Network Solution
- Secured Edge Platform
On one side the OT domain (Operational Technology – the factory part) usually stays strictly isolated from the IT infrastructure, whereas business flexibility and operational constraints encourage and sometimes impose interconnection. On the other side old systems are usually widely deployed, vulnerable to exploits and occasionally cannot be upgraded.
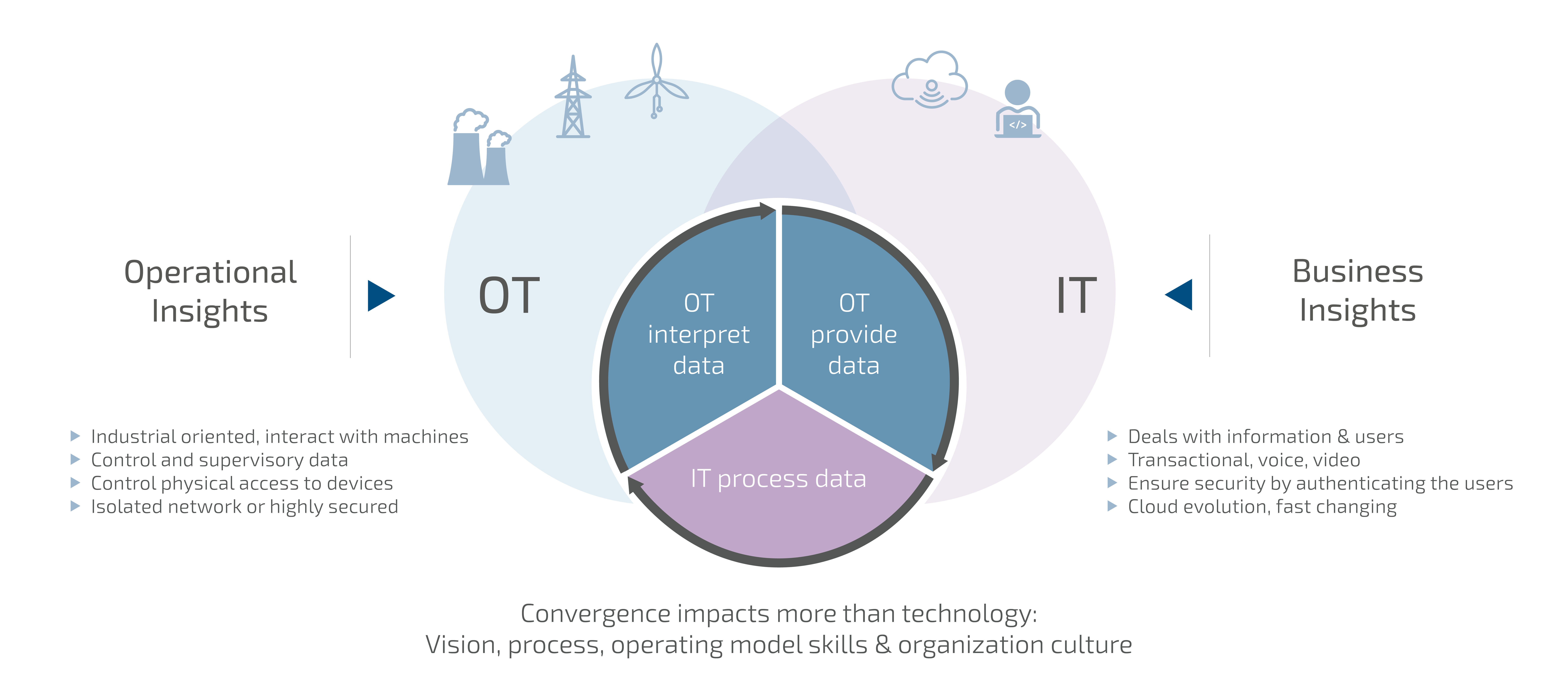
Convergence impacts more than technology - Vision, process, operating model skills & organization culture:
Operational Insights:
- Industrial oriented, interact with machines
- Control and supervisory data
- Control physical access to devices
- Isolated network or highly secured
Business Insights:
- Deals with information & users
- Transactional, voice, video
- Ensure security by authenticating the users
- Cloud evolution, fast changing
In order to allow old installed base to enter a second life, the Cyber Security issue must be addressed.
Part of a global fortress, an innovative Secure Xchange Network solution can prevent network level attacks from targeting the critical legacy system. The SECLAB SXN is an ANSSI certified product which allows file exchanges or application data flow between two isolated network domains. Data encryption shortly after the creation of the sender will make it nearly impossible for third parties to gain access to the data. Cryptographic keys are used to encrypt and decrypt data for the exchange. The end-to-end encryption protects the secret key and guarantees the highest encryption standard for communication, rendering man-in-the-middle attacks and other forms of data breaches ineffective.


The valid communication flows are rebuilt or even translated (for some legacy protocols) at the gate with no direct communication, and the legacy network stays completely hidden.
With such hardware enforced cross-domain gateway, every legacy system can remain connected for an extended period of time, with no need for patch at the OS or network level.
