Industry 4.0 and the Smart Factory promise a boost for innovation in the production sector. However, corresponding IoT security measures are still only beginning to develop, according to a study by the German Federal Ministry for Economic Affairs and Energy (BMWi) on “IT Security for Industry 4.0”. The core element of the Fourth Industrial Revolution is an increasing interconnection between industrial production and modern information and communication technologies. In the age of IoT, this exchange of data must be rigorously protected to avoid losing a technological advantage to competitors or well-organized hacker groups.

Safeguarding connected systems is the silver bullet (Quelle: www.pixabay.com).
IoT as a Blessing and a Curse for Users
Many users have mixed feelings about new developments in IoT and Industry 4.0. On the one hand, they offer hard economic advantages: Intelligent factories put out higher quality goods faster at lower costs and are more flexible and adaptable than their analog counterparts. But on the other hand, they offer new targets for attacks and leave users concerned that IoT applications may open up their virtual doors to cybercriminals.
75 Percent of IT Security Programs Have Critical Vulnerabilities
These fears are confirmed by security specialist RSA‘s latest “Cybersecurity Poverty Index Report”. IT and security experts from 878 companies, 24 sectors, and 81 countries were asked to assess their organizations’ maturity with respect to IT and IoT security. The results are sobering: Around three quarters of IT security programs in both the private and the public sector still have critical vulnerabilities. Respondents see the inability to respond quickly to IT security issues as the most troubling issue. Almost one half said that their Incident Response was “ad hoc” or “non-existent”; only a clear minority had worst-case strategies in place. And there is another key finding to add to the picture: Many companies invest in security only after they have fallen victim to a business-relevant attack.
IoT Security as a Central Element to Digitalization Strategies
Kontron’s approach is different and begins much earlier. We see security as the most important aspect in winning user trust for the operative use of new technologies. This is true today for existing applications, but will be even more so for future ones in IoT. Users will accept, work with new applications and profit from doing so only if they trust them. This is why we see IoT security as a central element to our customers’ digitalization strategies and have, accordingly, made it a key feature in all our products. A hardware basis that comes with integrated security mechanisms significantly facilitates the implementation process of IoT applications, increases product development efficiency, and makes our customer designs more future-proof.
First Mover in Embedded IT Security
To make this vision come true, we have developed a completely new hardware security product line. Kontron Security Solution makes us the first embedded computing manufacturer to offer fully integrated protection as a standard in our computer-on-modules (COM) and motherboards.
IoT Security by default: Kontron’s COMe-cSL6 is provisioned with a security chip to enable the support of Kontron’s Embedded Security Solution.
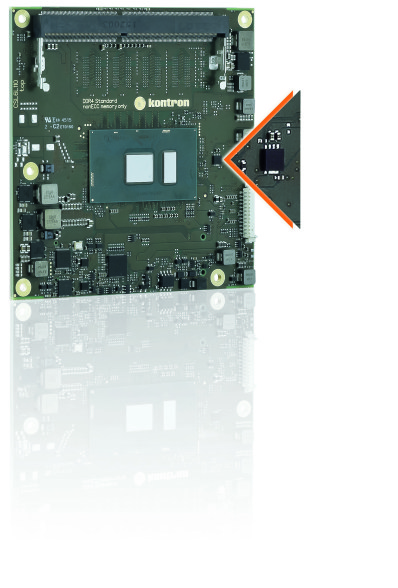
IoT Security by default: Kontron’s COMe-cSL6 is provisioned with a security chip to enable the support of Kontron’s Embedded Security Solution.
The new product line offers numerous security mechanisms such as IP and Integrity Protection; License Creation, Management, and Tracking; License Model Implementation; as well as the possibility to define different access rights. The first Kontron Security Solution product is the combined hardware and software solution Kontron Approtect. It comes with an embedded hardware security module as well as a software framework that unites comprehensive security functions such as IP and copy protection. All Kontron products with 6th generation Intel® Core™ processors are from now on equipped with the “Kontron Standard”, i.e. come with a hardware-based, integrated security solution. Products that have already been shipped can easily be upgraded.
Kontron Approtect is designed “As a Service”, resulting in lower costs for users. The solution can easily be integrated in existing infrastructures or already embedded with our hardware products. No complex changes to the IT infrastructure are necessary. The unique feature of our Security Solution Line is: It offers security in all use cases, even after delivery. We make sure that your IT is protected in the IoT, so you can fully concentrate on your work.

{{comment.comment}}